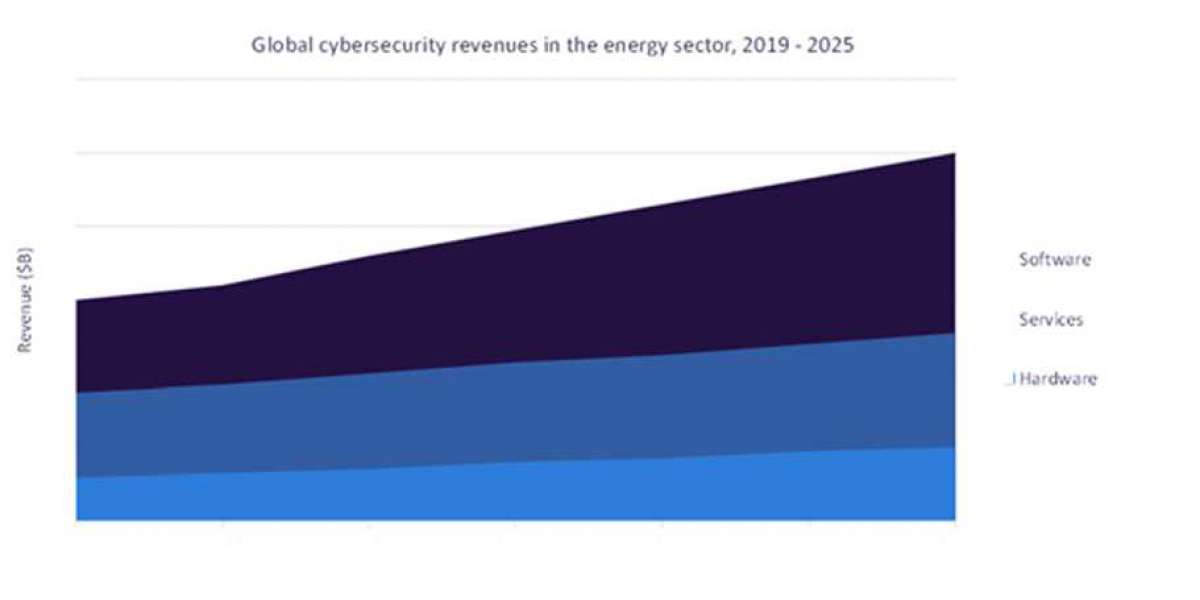
Protecting these critical infrastructure assets from cyber threats is essential to ensure the reliable and secure supply of electricity to homes, businesses, and essential services. Here are some key aspects of "https://www.globaldata.com/store/report/cybersecurity-in-power-theme-analysis/?utm_source=off-pageutm_medium=blogutm_campaign=off-page">cybersecurity in the power sector:
Threat Landscape: The power sector faces a wide range of cyber threats, including nation-state actors, hacktivists, criminal organizations, and insider threats. These threats can lead to disruptions, financial losses, and compromise of critical infrastructure.
Regulations and Compliance: Many countries have established regulations and standards for the power sector to ensure cybersecurity. Compliance with these regulations is essential to protect critical infrastructure and avoid legal repercussions.
Network Security: Securing the power grid's communication networks is vital. This includes protecting against unauthorized access, data breaches, and the potential for remote attacks on operational technology (OT) systems.
Security Assessments: Regular security assessments and penetration testing help identify vulnerabilities in the power grid's infrastructure, allowing for proactive mitigation measures.
Incident Response Plans: Developing and regularly testing incident response plans is crucial. These plans help in reacting swiftly to cyber incidents, minimizing damage, and restoring services as quickly as possible.
Employee Training: Training staff at all levels of the organization is essential. Employees should be aware of cybersecurity best practices, phishing attacks, and the importance of strong passwords.
Secure Supply Chain: Ensure the security of the supply chain for power sector components. This includes assessing and mitigating risks in the procurement process to prevent the introduction of compromised hardware or software.
Encryption: Implement strong encryption methods to protect sensitive data and communications, both within the organization and in data transfers between different entities in the power sector.
Access Control: Restrict access to critical systems and data based on the principle of least privilege. This limits the potential damage that can be caused by insiders or external threats.
Monitoring and Intrusion Detection: Employ robust monitoring and intrusion detection systems to detect and respond to any unusual or unauthorized activities on the network promptly.
Collaboration: Share threat intelligence and best practices with other power sector organizations, government agencies, and cybersecurity professionals to enhance collective security.
Resilience: Enhance the overall resilience of the power grid by building redundancy into critical systems, having backup power sources, and preparing for worst-case scenarios.
Patch Management: Keep software and systems up to date with the latest security patches to address known vulnerabilities.
Public Awareness: Educate the public about the importance of cybersecurity in the power sector and how they can play a role in reporting suspicious activities or threats.
Continual Improvement: Cybersecurity is an evolving field. Regularly assess and improve your cybersecurity measures to adapt to new threats and technologies.
The power sector is a critical infrastructure, and a successful cyberattack could have severe consequences. Therefore, a comprehensive and proactive approach to cybersecurity is necessary to protect the power grid and ensure the continued delivery of electricity to society.
For more insights on the cybersecurity value chain in power theme, buy the full report or "https://www.globaldata.com/store/talk-to-us/?report=1926470">download a free report sample